When you first begin to study eDiscovery, you’ll likely start out learning about this particular image:
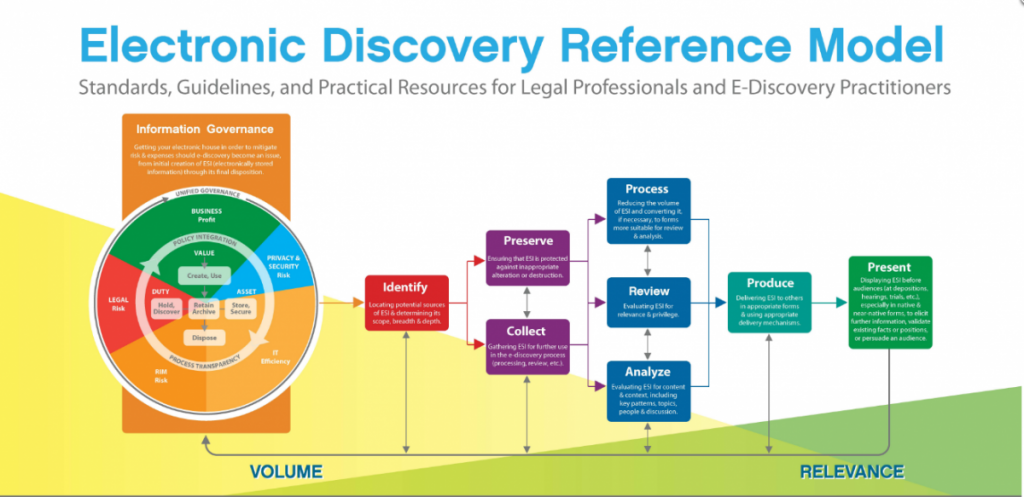
The eDiscovery Reference Model has been around for quite a while and it has done a fairly decent job of displaying the eDiscovery process in an easy-to-understand manner. But, I’ve always felt that the big IG rectangle-wheel-chunk was just more of an afterthought. It doesn’t have the simplicity that a novice would need, nor the depth that a veteran would appreciate. I think if you were to ask legal technology students/professionals, they probably will admit to simply ignoring that part of the EDRM.
So, to simplify the topic a bit (and in keeping with the EDRM), I’ll split the IG information into boxes like so:

Information Governance is basically the study of how to “use” and “organize” a company’s data to achieve 2 goals:
- Keep regulatory risks low: every business in every industry has rules and regulations (government-issued or not) that they must follow. The goal here is to make sure those rules aren’t violated or inadvertently causing the business issues.
- Gain the most value out of the data: making money is hard, for corporations and for individual people. So, with all the information that we learn, receive, and generate each day, it would be great if we can re-use any existing data we already have. It would be even better if we can create new ideas/efficiencies from that same data.
With those goals in mind, Information Governance can basically be broken into 5 components (or processes that work towards those goals):
Organization. Know where the information came from, where it is stored, how it flows through the business, and how it can be retrieved as needed:
- How much data does the company have?
- How much new data is generated on a regular (monthly, quarterly, annually, etc.) basis?
- Where did the data come from – how does it move through the company?
- What kind of data does the company have (data types, subject matter, age, etc.)?
- Where/how is the data stored? Also “why” – why do all the files from origin X go into network drive Z?
- Who are the individuals/departments responsible for the data?
- Who are the individuals/departments who often access the data?
Security. Ensure that information is protected from accidental changes/deletion and assessable only by authorized users:
- Physical Security.
- Cameras, guards, mantraps, etc.
- Biometric locks
- Time/location-based locks on laptops and other mobile devices.
- Electronic Security.
- Implementation of “least privilege” access
- Password hashing and salting
- Encryption at rest, in transit, and in use
Compliance. That the information is stored and used in accordance with relevant rules and regulations:
- How is the data being used?
- What regulations apply to the business/data? (HIPPA, SOX, GLBA, COPPA, FERPA, PCI-DSS, CCPA, etc.)
- Who has access to the data?
- How is the data made accessible to third parties?
- What are the required retention periods?
Knowledge Management. The knowledge garnered from the information can be used to generate new ideas and elevate the business’ capabilities:
- Identify, classify, and organize the knowledge to make it easier for retrieval and use (taxonomies for current vs future use, department needs, end-use goals, etc.)
- Identify knowledge gaps.
- Extract information that’s useful for operations to create project accelerators (templates, best-practice guidelines, automated scripts, etc.)
- Continually assess, update, and validate the knowledge base.
Disposal. Information that is no longer relevant/outdated should be properly and securely destroyed or archived as needed:
- Aim to delete unnecessary information at the earliest point (data deleted as part of the “ordinary course of doing business” is “safe” from litigation, anything not disposed of is fair game to an RFP).
- Establish a framework for managing the internal information lifecycle.
- Select the correct disposal tools (shredding, degaussing, overwriting, etc.)
- Regularly audit the disposal program and update as the needs of the organization change.
And there we have it. Not as pretty or elegant, also much wordier – but overall I think it’s a simpler explanation of “information governance”.



